Cerber ransomware introduces malware coordination via the bitcoin blockchain
In order for a malware author to exchange status information and instructions with the infected clients, a coordination server or command & control server (C&C) is necessary. This server is often the weakest link in the operation, as blocking or taking it over will render the botnet harmless. As a result, we have seen many innovations over the years to run this coordination in a more stealthy and resilient way, leading to the replacement of IRC with HTTP, the introduction of P2P and hybrid C&C channels, and the development of domain generation algorithms.
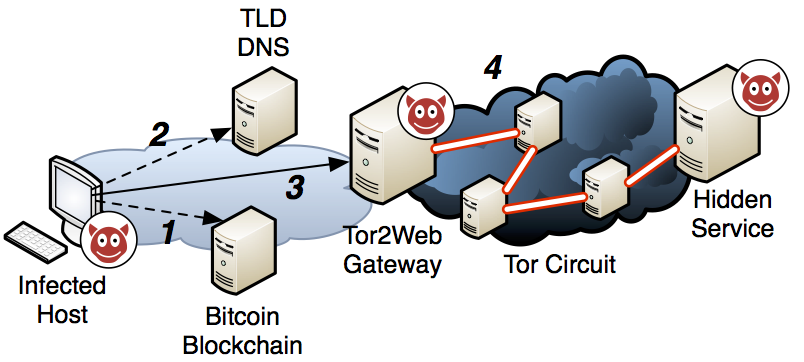
The Cerber ransomware introduced something entirely new, namely the dissemination of information to the clients via the bitcoin blockchain. By making bitcoins from specific coordination addresses, the malware owner can tell all infected hosts about the address of the coordination server, and if necessary issue an update than is effective instanteneously. As a malicious account in the blockchain can by design not be suppressed, this makes response to this new step in the malware evolution challenging. This is the most recent step in the evolution of this cat-and-mouse game.
Over a period of 15 months, we have observed the evolution of this new coordination principle in the wild, and how criminals adapt their techniques and procedures to respond to getting detected and blocked. We have written up the story in a research post and in a paper presented at IEEE Communication and Network Security.