Is CTI a product without a process?
What's wrong with CTI and what we should focus on
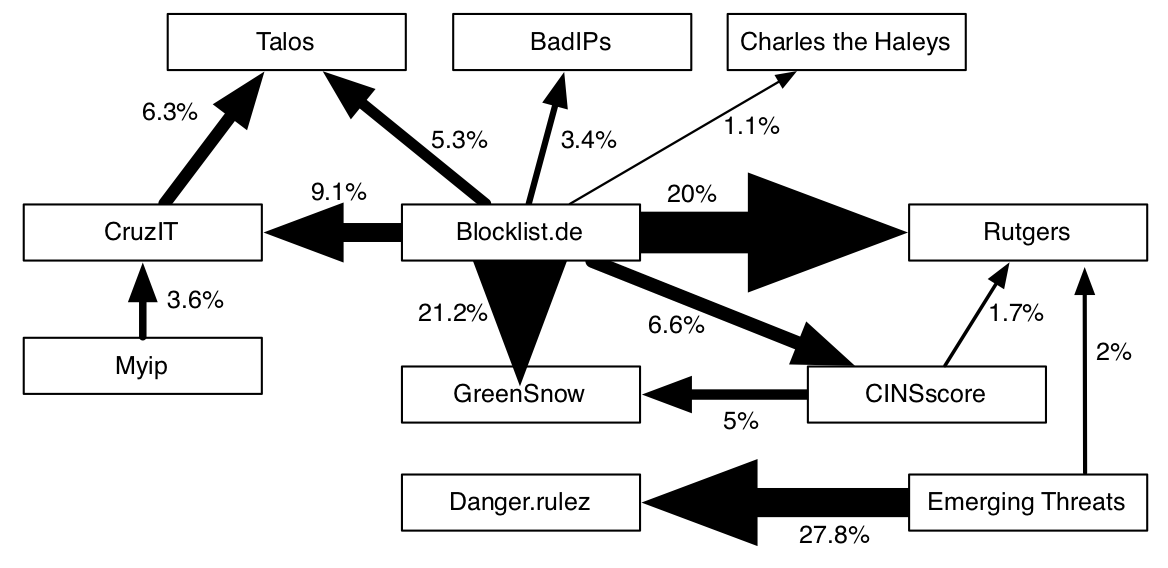
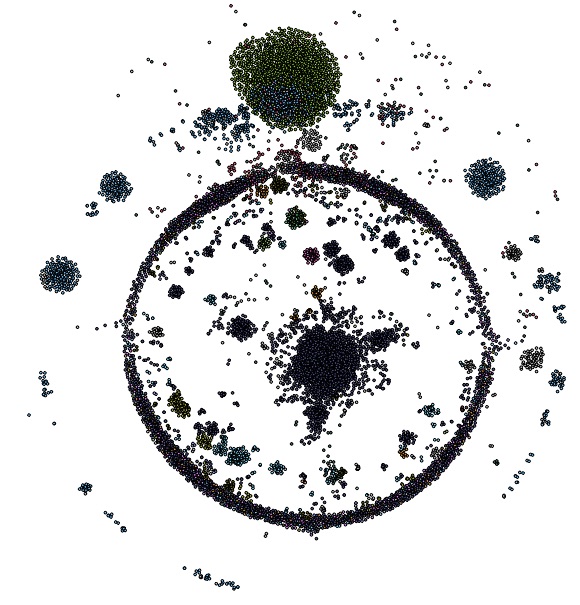
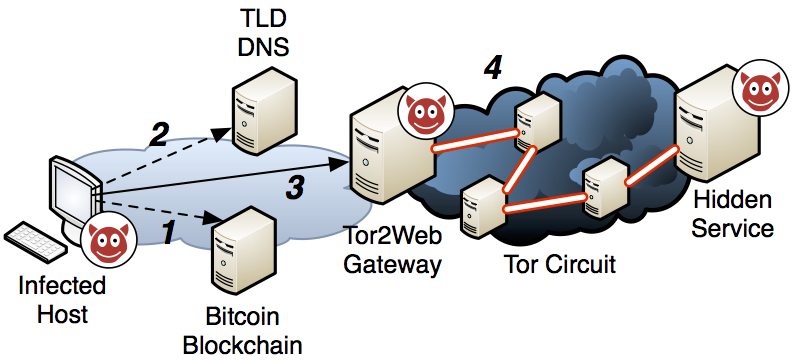
Cyber threat intelligence has become an important component for today's cyber security practice, but its great potential is frequently not fully realized. In our latest position paper, we take a look at the state of the cyber threat intelligence field. We argue that CTI is still in its infancy, and is rich with tools and technical knowledge, but comparatively light still on process and methdology. This is where the biggest potential lies for the advancement of CTI, because a good product is the result of a solid process.