Cryptojacking - Malicious, invisible exploitation of website visitors
Cyber criminals are able to earn money by using your computer, without you installing anything on your computer and without you being aware of it. In this research, we are reporting on attackers deploying large cryptojacking campaigns spread over numerous websites exploiting their visitors for illicit cryptomining
What is Cryptojacking?
Cryptocurrency -- such as Bitcoin, Ethereum or Monero -- is mined by computers solving a cryptographic puzzle, which gets increasingly difficult over time. With the increasing popularity of Bitcoin, so many people started mining using their computer that this was no longer was profitable to do, so people turned to mining bitcoin using their graphics cards. By now, this type of mining is also no longer effective and professional bitcoin miners are relying on custom-made chips to create coins.
As Bitcoin mining cannot be efficiently done anymore using regular hardware, a lot of alternative cryptocurrencies have sprung up over the past years, which modified the way mining is done. One of them is Monero, which uses a different type of cryptographic puzzle that is well suited for normal PCs but cannot be efficiently parallelized using specialized hardware. Thus in order to obtain Monero at scale, you will need access to a lot of computers.
These new cryptocurrencies and web-based mining have also attracted the attention of cyber criminals. Over the past 18 months, criminals have begun to systematically hack websites and compromise software, and embed these scripts so that they can earn a profit from unsuspecting users. When cryptomining is done without knowledge and consent of the user, we refer to it as cryptojacking. The Cyber Threat Intelligence Lab has investigated the use and scale of such cryptomining scripts by cyber criminals among 55 million web pages, and we have found hundreds of actors exploiting the attack vector in a coordinated fashion. In this blog post, we highlight a number of key findings of our research. Please refer to the full paper if you want to know more about this research.
Cryptojacking Prevelance
In order to see how widespread the problem is and how these attacks are deployed in practice, we need to measure a large part of the Internet. While often Internet surveys are done using top lists such as the Alexa Top 1 Million -- a directory of the one million most popular websites on the Internet --, this will not create a true insight into the problem. As cryptojacking is more profitable the more people visit the website, you would expect websites ranking at the top to be over-proportionally engaging in this practice. Instead of compromising a single large website, you could also diversify and target hundreds of different ones, so your earnings are more robust if owners spot the compromise and remove it.
We built a crawler to detect cryptojacking and analyze how it was deployed on a particular site. With this system, we go through two parts of the Internet, first we visit the top websites according to Alexa, Majestic and Cisco, and second, we visit 20% of all websites of the Internet, randomly sampled from 1136 top-level domains such as .com, .org etc. Over a period of 3 months, 720 of our crawlers visited 55 million websites and followed those which were infected with cryptojacking.
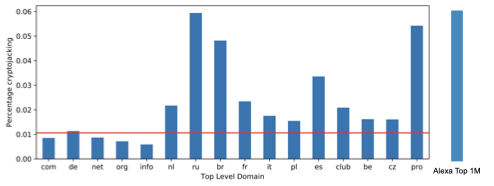
Indeed cryptojacking is much more widespread across the most visited parts of the Internet -- about 0.06% of all websites in the Alexa Top 1 million engage in this practice --, as it is much more profitable to do it there. The likelihood to find cryptojacking here is approximately 5 times as large as in the Internet as a whole. While across the entire Internet only 0.011% of all websites were actively cryptojacking during our study period, there is a large difference between the various top-level domains. When you visit a Russian and Brazilian domain, the change to find cryptojacking is five times as high than for example on a German domain or .com in general. Different countries also have clear preferences for the type of providers they choose when doing cryptojacking.
Organized Campaigns are Widespread
While infecting a major website such as amazon.com with cryptojacking would create a lot of earnings, it would probably also get very soon be noticed. Another strategy is thus to target a large number of websites, each with a few visitors, and thus make money through volume.
If you would be targeting hundreds of websites, it is however impractical to setup hundreds of Monero accounts and deploy different attack scripts and supporting infrastructure for each website. Instead, it is much easier to channel all money through just a few accounts, and reuse the Javascript files required for cryptojacking across the individual sites.
When criminals take this easy route, this will also allow us to group those websites together which are under the control by the criminal. When the cryptojacking on two websites sends the earnings to the same account or both are using the same proxy server for their activity, we can link them as related. In our crawler, we perform this type of analysis across a number of dimensions, including how the cryptomining code is implanted into the website and how it is being called, a so-called stack trace.
We discovered the existence of 204 cryptojacking campaigns, ranging from just a few compromise websites to gigantic installations involving up to 987 websites in a single campaign all generating money for the same actor. By both manual and computer-assisted stack trace analysis we found out that most of these cryptojacking campaigns were the result of the abuse of vulnerabilities within the
third-party Web software ecosytem. We have seen crimininals installing cryptojacking scripts on a large number of websites running an out-dated version of WordPress, and we found websites to be using pirated version of premium WordPress themes which are accompanied by a cryptominer script. By spreading such scripts through pirated copies
of premium WordPress themes, attackers were able to infect almost a 1000 websites with the same infection.

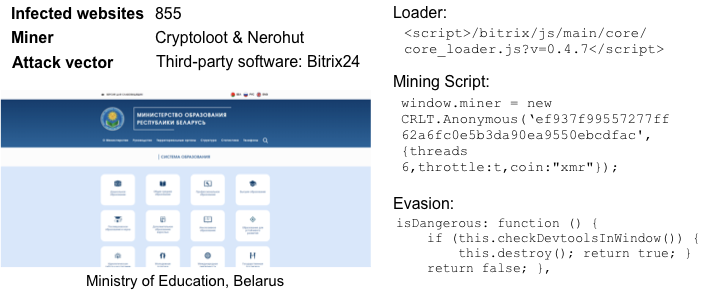
Not just WordPress is abused by these cyber criminals, also Bitrix24, a CRM system used by a large number of campanies all over the world has been a victim of this attack. A maliciouos file, disguised as the Bitrix24 core loader, contains a number of different miner scripts which are randomly chosen upon visit. The infection even included an evasion technique, which stops all mining operations happening on the website once the Developer Tools window is opened.
Third-Party Software is the Most Common Attack Vector
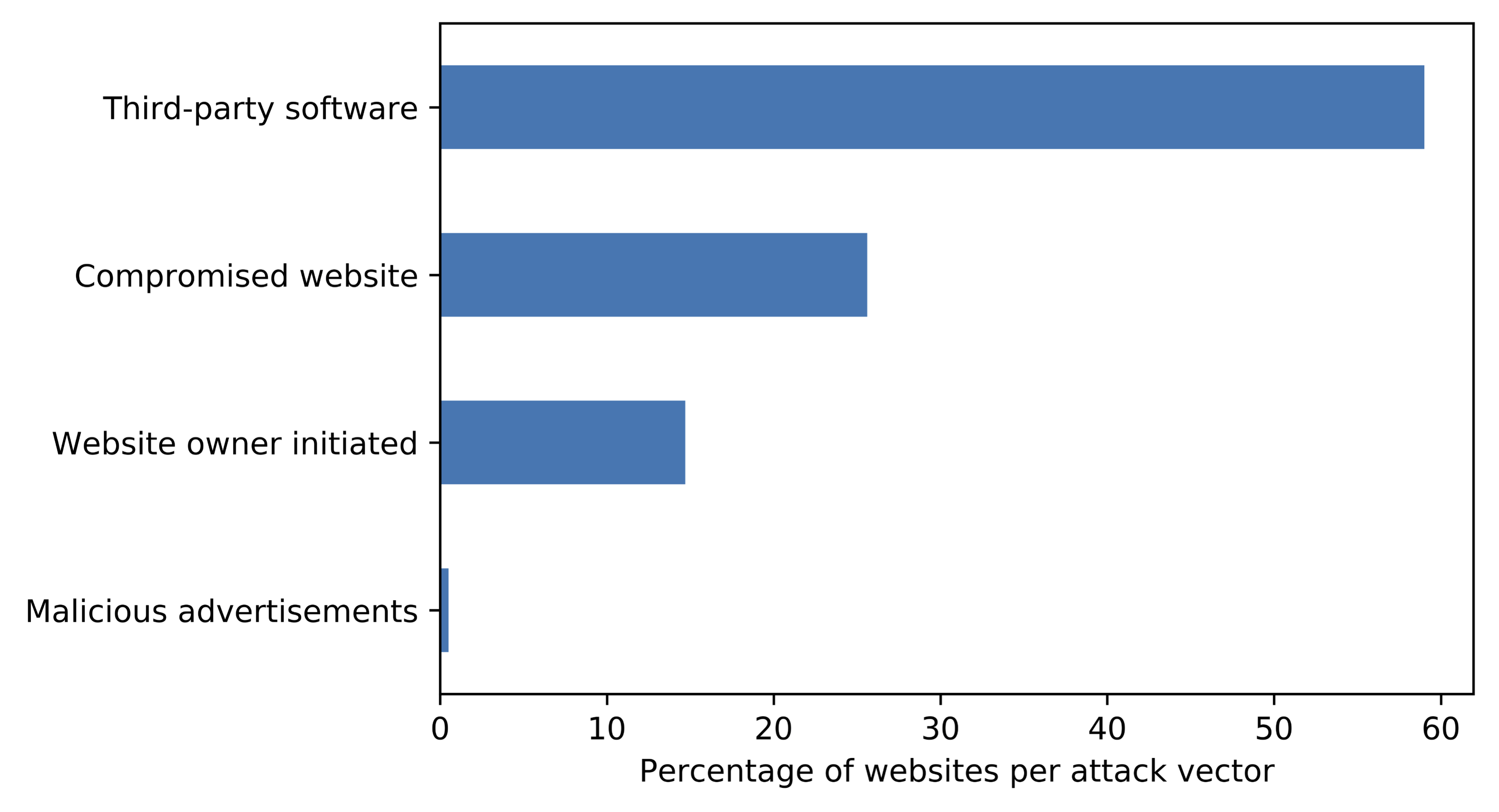
By looking at all these campaigns, we noticed that attacks like these were responsible for a large share of cryptojacking in the Internet. In fact, when we trace how a website got infected, almost 60% of all cryptojacking infections among the identified campaigns are the result of a compromise of some third-party software, such as a content management system plugin, a (pirated) template, or a hosted library.
Less than 30% of all infections are the result of a (regular) hacked website, and less than 15% is put up by website owners themselves. While we frequently hear about malware infections due to malicious advertisements, this attack vector is only vanishingly small with respect to cryptojacking.
This surprising distribution is noteworthy in two respects: first, it again shows that the "popular parts" of the Internet -- facebook, google, amazon and so on -- and structually very different from the Internet at large.
Across these top sites, we do not find content management systems such as Wordpress or Joomla, with outdated installations and plugins, pirated templates and externally hosted code which is abused through these campaigns, however in the general Internet we do. Second, the findings highlight that we are not doing great in securing today's software ecosystem, which are highly entangled and getting increasingly complex, and better steps are needed to secure modular ecosystems such as marketplaces with add-ons, plugins and other external components, so that users can be certain on what code is actually running.
Downloads
You can read more about our analysis of cryptojacking in our report below:
Hugo L.J. Bijmans, Tim M. Booij and Christian Doerr, Inadvertently making Cyber Criminals Rich: A Comprehensive Study of Cryptojacking Campaigns at Internet Scale, Usenix Security Symposium 2019 [pdf]


